System Overview
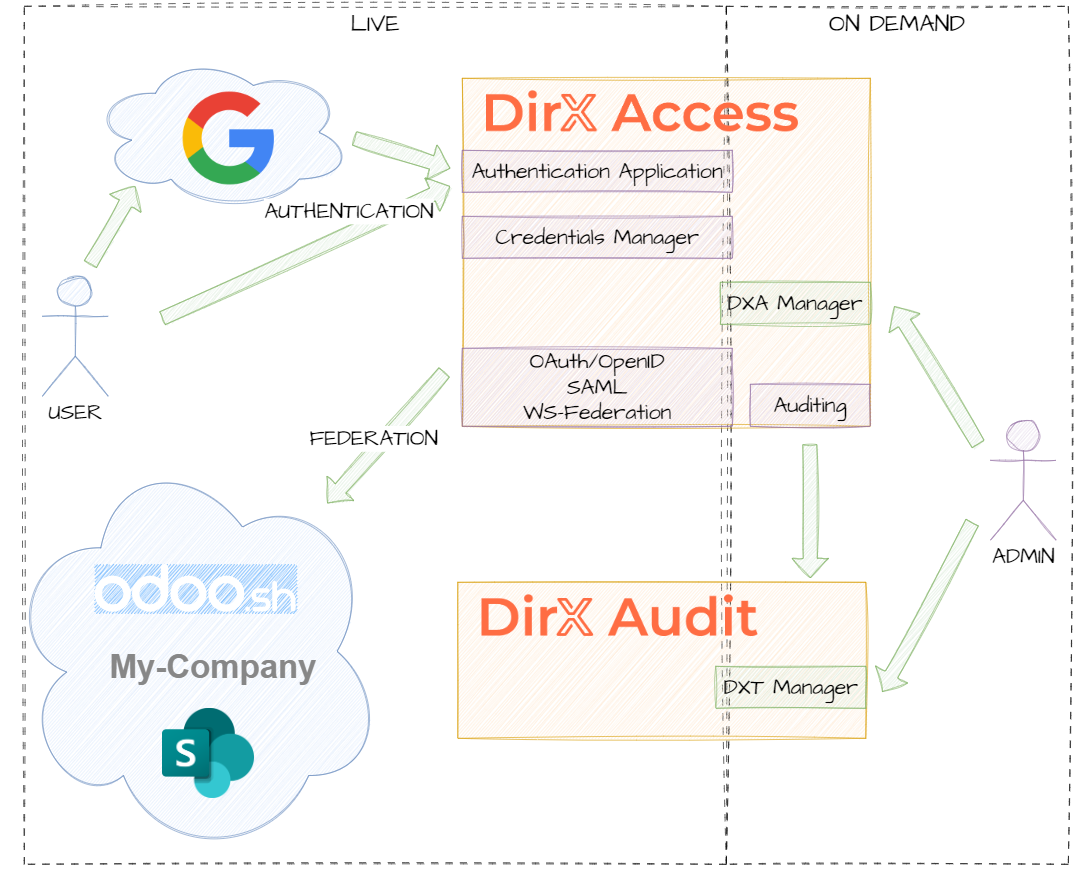
The diagram below explains how authentication and federation work in the DirX Access Demonstration server, the system manages user access, authentication and auditing. Anyone can try out the system features from the role of user - please follow the specific scenario pages from the left menu.
Demonstration of additional capabilities (e.g., auditing) is available on-demand.
Links
Federation
In Identity and Access Management (IAM), federation is the process of linking identities across multiple systems or organizations, allowing users to access different applications with a single set of credentials. It enables Single Sign-On (SSO) by using trust relationships between identity providers (IdPs) and service providers (SPs).
Within this Demonstration scenario, anyone has the possibility to try out how federation enabled by DirX Access seamlessly interconnects different applications. Please, follow:
-
Choose one of the protected applications (SPs):
- My-Company - Mockup web pages of a made-up company
- Odoo - CRM application residing in a public cloud; To access the Odoo CRM application, the account has to have an e-mail registered within the Credentials Manager.
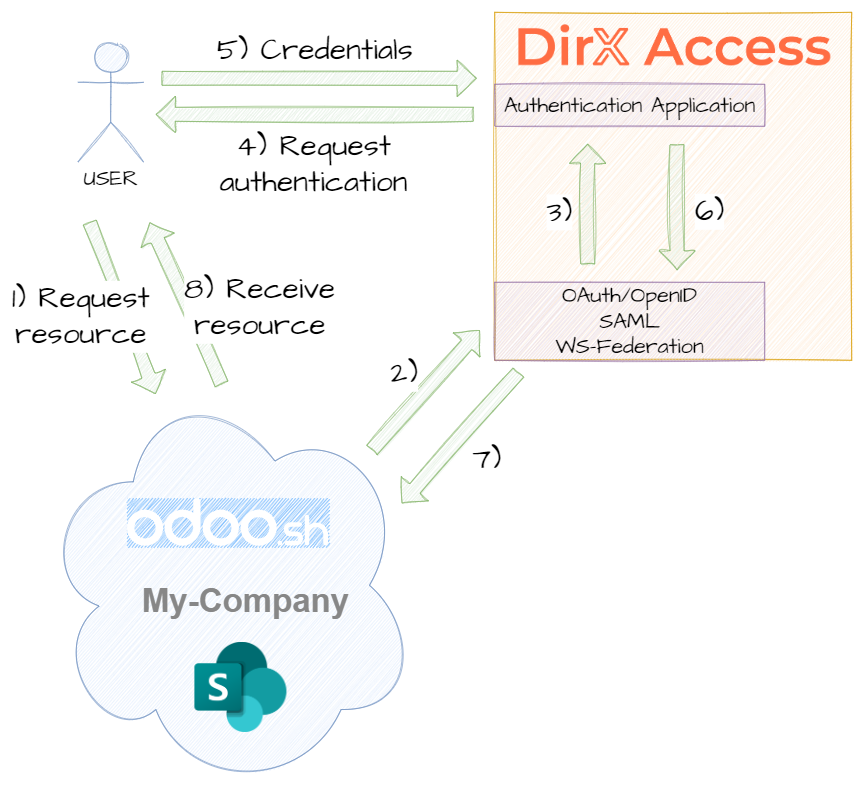
- When accessing the link, you'll be automatically redirected to DirX Access Authentication Application.
- In the Authentication Application, there are multiple options of user authentication. You can choose any type, supposing you have already registered credentials for it. If you don't have the necessary credentials or you don't have any account yet, please, visit the Registration and Account Management tab.
- After successful completion, you are automatically redirected to the original link of the protected application with your identity.
- Accessing any other protected applications from now on follows the single sign-on principle and doesn't require any further authentication as the information about your identity is already part of the current session.
Registration and Account Management
As an authentication provider, DirX Access natively supports registration of all the different types of credentials for the authentication methods it offers. The registration and subsequent credentials management is possible via the Credentials Manager application.
The Demonstration Scenario enables registration of a new user with username/password credentials.
For a registered account, it is possible to:
- manage all credentials (create new ones, change and remove existing ones),
- register and unregister E-mail being part of the DirX mailing list.
Subsequently, it is possible to register for existing user the FIDO/WebAuthn credentials (in some context also known as Windows Hello for Business).
In production deployment, the Credentials Manager might also serve to the help desk staff to unblock accounts blocked due to invalid authentication attempts (e.g., exceeding the allowed number of subsequent login attempts with invalid password).
Google Integration
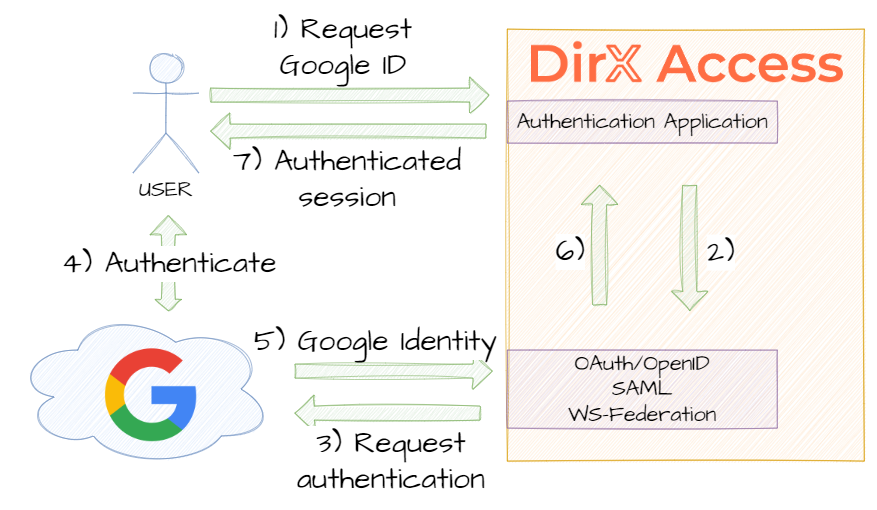
In the Google Integration demonstration scenario, the role of DirX Access is switched - DirX Access consumes the identities provided by Google.
- In the Authentication Application, choose the Google option.
- You will be redirected to the Google authentication.
- Authenticate in Google and you will be redirected back to DirX Access.
- DirX Access creates a session for you, which can be used for accessing the protected applications.
While DirX Access generally enable to store the - so called - Just-in-time resolved identities and further manage them, this feature is currently not enabled in the demonstration scenario.
Risk-based Authentication
Achieving security is always about finding a balance between what is effective and user-friendly on one side and what is secure enough on the other. While the administrator could let everyone authenticate using complex multifactor authentication methods right at the gates of the system, it could be unnecessarily complicated supposing the system contains resources requiring different level of protection.
From these reasons, DirX Access enables to set up the risk-based authentication policies. These policies evaluate following aspects:
- the requested resource context,
- requesting user and its habits,
- access time, IP address, etc.
and based on them assign a risk level to each request. User then has to use secure enough authentication method to balance out corresponding risk level.
This system demonstrates the risk-based authentication on a simple scenario. Two resources are assigned two different risk levels. If you try to access them, you will be asked for two different types of authentication methods.
Of course, also in this case the SSO is active, meaning, if you have already authenticated with secure enough authentication method within existing session, you will not be prompted to reauthenticate.
Demo Guide
Welcome to the DirX Access Demonstration Scenario!
These pages can guide you through the most common scenarios covered by the DirX Access product. DirX Access specializes on user authentication, single sign-on, identity federation, and authorization within complex heterogenous systems.
Following list may help you to smoothly go through the whole demonstration. Each action is described more into detail at its own tab found in the left menu.
Register new user account at Registration to be able to authenticate yourself in subsequent steps. You can choose arbitrary username and password.
Demonstration scenario also enables to try out other forms of authentication. These are also necessary for accessing high-risk resources later in the scenario.
TOTP credentials registration requires sharing a secret between DirX Access and TOTP calculator application. DirX Access provides the shared secret in a form of QR code that can be consumed by most of the contemporary TOTP authenticator mobile apps.
FIDO or WebAuthn registration is performed via DXA Authentication application via the Registration -> FIDO Registration link. You have to possess some form of FIDO/WebAuthn authenticator (e.g., Windows Hello, Apple FaceId, dedicated FIDO-enabled token, etc.). FIDO registration requires to authenticate first via existing username and password and then the action is completed.
Any of the credentials can be subsequently managed via the DXA Credentials Manager.
Browse protected resources at My-company (representing a third-party protected application) and witness seamless integration with authentication capabilities of DirX Access.
Browse protected cloud resources at Odoo which is a cloud-based CRM tool. To enable this, user has to register their e-mail address in DXA Credentials Manager.
Request high-risk resource and see the enforcement of more secure authentication.
User shall be redirected to DXA Authentication Application with limited list of enabled authentication methods. Hence, to successfully perform this scenario, either TOTP or FIDO credentials have to be registered.
Choose Google authentication method in the DXA Authentication Application and authenticate in Google. You will be redirected back to DXA with a session created for you.